You can have the best-designed Cloud application in the world, but it will all come crashing down like a house of cards if you don’t properly secure it. Even small blind spots can cause a massive headache that could cost your business time, money, and reputation. That’s why cloud security should be the priority-zero when it comes to building your AWS infrastructure.
Security isn’t just a “nice-to-have”. It’s also part of your duties under the AWS Shared Responsibility Model. Fortunately, AWS doesn’t make you do all the heavy lifting, and provides a number of great tools that you can use to build a really robust security infrastructure on AWS.
Let’s take a dive into the AWS Shared Responsibility Model, and the tools you can use to meet your responsibilities.
What is Cloud Security?
Cloud security refers to the measures and practices that are put in place to protect data, applications, and infrastructure associated with cloud computing from threats and vulnerabilities. This can include measures such as encryption, access controls, and network security to protect data in transit and at rest. Cloud security also involves the use of security tools and services provided by cloud providers, such as Amazon Web Services (AWS) and Microsoft Azure, to monitor and protect cloud environments. The goal of cloud security is to ensure that data and resources in the cloud are protected against unauthorized access, misuse, and other threats.
How Does The AWS Shared Responsibility Model Work?
There are two clear areas of responsibility when it comes to AWS security. Those are your responsibilities, and those covered by AWS. Generally, you are responsible for security in the cloud, and AWS is responsible for the security of the cloud.
As a starting point, you are responsible for managing guest operating systems, application software, and proper configuration of AWS supplied security controls. The exact scope of your responsibilities will vary depending upon which services you use, and how they are integrated with your own IT environment.
A general overview of the typical distribution of responsibilities between the customer and AWS:
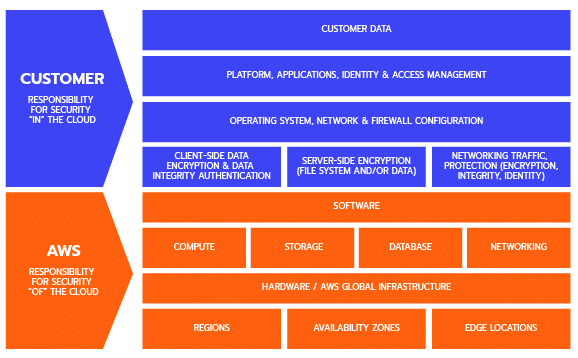
As a rule of thumb, the more managed services a customer opts to use, the less direct responsibility for security it will have. As you shift from using AWS as Infrastructure as a Service (IaaS) provider, towards a Platform as a Service (PaaS), AWS’ responsibility increases. This is particularly useful for teams that lack a large InfoSec department, or want to free them up to focus on other responsibilities.
Generally, the more security responsibilities you can move to AWS’ side, the better. They are experts in this, and are way better equipped to manage the risks that come with running the largest public cloud. This frees your hands to focus on the big picture.
With that out of the way, let’s take a look at some of the security features provided by AWS, and how you can best leverage them.
Encryption – Your First and Last Line of Defense
We talked a lot about encryption in our previous article, but it really does need repeating: Every single AWS user needs to use encryption. It helps to protect files that are compromised, and can prevent a small data breach transforming into a complete disaster.
So how does it work? Encryption scrambles data so that it becomes unreadable without a special key, known as a cipher. A cipher contains all the information necessary to decrypt the data, making it readable. This means it is possible to send data, safe in the knowledge that only a party with the right “key” can read it. Encryption is particularly important when dealing with sensitive data, like passwords, but in reality encryption should be used everywhere.
While you could manage your own encryption, AWS provides built-in encryption for Elastic Block Store (EBS), Simple Storage Service (S3), Relational Database Service (RDS), and Redshift. Additionally, the AWS Key Management Service (KMS) can help you safely store, rotate keys, offloading some of that security responsibility from you, and onto AWS.
Infrastructure Security – Stop Attackers Before They Get Access
Infrastructure security refers to the tools that prevent unauthorized access to your Cloud implementation in the first place. This covers a range of different tools that all have their own unique role in cloud security.
AWS VPCs
AWS VPC is a managed service that enables you to control the kind of traffic going in and out of your application resources. You can set up rules to prevent contamination from spreading, for example by blocking outbound Server Message Block (SMB). You can even transfer your organization’s existing firewall rules, as AWS Network Firewalls understand rules written in common open source rule formats.
Additionally, you can integrate AWS Network Firewalls with managed intelligence feeds sourced through the AWS Marketplace. You can manage everything through the AWS Firewall Manager, so once you build policies and rules, quickly apply them across your VPCs and accounts.
DDoS Mitigation
AWS comes with a number of tools that can help defend you against a Direct Denial of Service attack. These attacks typically involve sending a large volume of traffic at servers in an attempt to overwhelm them, and disrupt the service.
AWS Web Application Firewall (WAF), is a good place to start. It protects web applications and APIs against commonly used web exploits and bots. It does this by allowing you control over how traffic reaches applications using security rules that block common attack patterns, like SQL injection, or cross-site scripting.
These rules are pretty granular, and can be configured to filter out specific traffic patterns, allowing you to react to evolving security threats. You can get started by using Managed Rules for AWS WAF, a pre-configured set of rules managed by AWS, or get rules lists from AWS Marketplace sellers. These typically target common security risks, for example the OWASP Top Ten security risks guidelines.
Another option is AWS shield, which is a managed DDoS protection service. It provides always-on detection, and means that you don’t need to engage AWS support. It comes in two tiers, standard, and advanced.
Every AWS customer gets access to AWS Shield Standard, which defends against the most common DDoS attacks. It provides comprehensive availability protection against all known layer 3 and 4 infrastructure attacks.
Some use-cases, such as applications running EC2 or ELB services, will require more robust protection: AWS Shield Advanced. It provides the same protection as standard, but also provides tools to deal with large and sophisticated DDoS attacks in near real-time. AWS Advanced Shield is fully integrated with AWS WAF, which is the most robust DDoS protection setup you can have.
Preconfigured Instances
It is also possible to use tools to create or shut down AWS resources, manage changes, obtain an inventory of cloud assets, and even use infrastructure as code templates to replicate known, tested, secure configurations. Additionally, you can run secure instances with tested EC2 Amazon Machine Images (AMIs), which enable you to create a standard, preconfigured, hardened virtual machine instantly.
Identity and Access Management
Empower admins to define what users can access in the Cloud. AWS Identity and Access Management (IAM) helps to define these roles at a high level. AWS supports secure login with Multi-Factor Authentication. Correctly configured, IAM makes it simple to follow the rule of least privilege.
Users can take advantage of AWS Control Tower to manage multiple accounts and teams. This helps managers easily set up and oversee their environments, and ensure that everyone has the accesses they need, and don’t have those that they don’t.
Monitoring and Logging
Another really powerful tool is AWS CloudTrail, which monitors your AWS cloud environment API calls, and console actions. Additionally, Amazon CloudWatch provides standardized log data from all AWS services, enabling you to understand your operational health at a glance. Finally, Amazon GuardDuty analyzes logs in real time in order to identify malicious or unauthorized activities in your Cloud deployment.
AWS Cloud Compliance
Aside from these technology specific tools, AWS also offers a way for you to ensure compliance with any local regulations that you must, by both the shared responsibility model and your local legal obligations, abide by.
AWS Artifact service includes third-party validation for thousands of global compliance requirements, from HIPPA to GDPR, and more. It is also possible to automate many of your compliance requirements, and even generate regular reports, so you can identify and rectify any areas where you believe that you may be falling short.
Our Tips On AWS Cloud Security Best Practices
There are a number of things that you should, and shouldn’t, do in order to maximize the security of your AWS implementation. To help you on your way, we’ve created this checklist:
✅ Encrypt your data
✅ Back up all your systems and data
✅ Limit your AWS Security Groups
✅ Ensure secure access to cloud resources
✅ Centralize all CloudTrail logs
🚫 Forget to set the authentication
🚫 Hard code your secrets
Need a Hand? Cloudvisor Is Here To Help
While AWS does a great job of providing tools to make it easy to secure your cloud, it can still be a little overwhelming to ensure that everything is working as it should. That is where you can bring in the experts to help you sleep soundly.
The Cloudvisor team is uniquely well-placed to serve startups. We are one of few AWS Advanced Tier Service Providers that also specializes in building AWS solutions specifically for Startups. This gives us unique insights into the security challenges startups face and helps us determine the most efficient way to help them meet their security obligations.