Take control of your confidential data with AWS Key Management Service (KMS), the essential tool every business needs to safeguard their information. With cyber threats on the rise and stricter data privacy regulations in place, protecting your data has never been more critical.
This guide delves into how AWS KMS can provide your company with robust encryption solutions, ensuring that your data remains secure and accessible only to authorized individuals. Whether you need to protect customer information, financial data, or sensitive intellectual property, KMS offers a comprehensive platform to meet your encryption requirements.
Table of Contents
Using industry-leading techniques and advanced encryption algorithms, AWS KMS allows you to manage your encryption keys securely and efficiently. From generating and rotating keys to auditing and monitoring their usage, KMS offers complete control and visibility over your data protection processes.
Don’t take chances with your confidential data. Discover how AWS KMS can help you strengthen your security posture, build customer trust, and comply with regulatory requirements. Safeguard your business with KMS today.
Understanding the Importance of Data Security
In today’s digital age, data security has become a top priority for businesses of all sizes. With the increasing frequency and sophistication of cyber attacks, companies must proactively protect their confidential data. A data breach can have devastating consequences, including financial loss, damage to reputation, and legal ramifications. Therefore, investing in a robust encryption solution like AWS KMS is crucial to safeguarding sensitive information.
AWS KMS offers a range of features and benefits that make it an indispensable tool for data security. First and foremost, it provides a secure and centralized location for managing your encryption keys. This means that you no longer have to worry about the security of your keys or the risk of losing them. With KMS, you can easily generate, rotate, and revoke keys, ensuring that your data is always protected.
Furthermore, AWS KMS integrates seamlessly with other AWS services, making incorporating encryption into your existing infrastructure easy. This ensures that even if your data is compromised, it remains unreadable without the corresponding encryption key.
Lastly, AWS KMS offers a high level of scalability and performance. As your business grows and your data protection needs increase, KMS can easily scale to meet your requirements.
In summary, data security is a critical concern for businesses today. By implementing AWS KMS, you can enhance your security posture, mitigate the risk of data breaches, and comply with data privacy regulations.
Overview of AWS KMS Features and Benefits
AWS KMS offers a wide range of features and benefits that make it an essential tool for every business. Let’s take a closer look at some of the key capabilities of KMS:
Secure Key Management
AWS KMS provides a secure and centralized location for managing your encryption keys. As mentioned, you can easily generate, rotate, and revoke keys, ensuring your data is always protected. With KMS, you no longer have to worry about the security of your keys or the risk of losing them.
Integration with AWS Services
AWS KMS seamlessly integrates with other AWS services, making incorporating encryption into your existing infrastructure easy. Whether you use Amazon S3 for storage, Amazon RDS for databases, or Amazon EC2 for computing resources, KMS can encrypt your data at rest and in transit.
Scalability and Performance
AWS KMS offers high scalability and performance, allowing you to handle large volumes of data and encryption requests. With built-in redundancy and automatic backups, you can be confident that your encryption keys are always available and protected.
Granular Access Control
AWS KMS allows you to define fine-grained access control policies for your encryption keys. You can specify who can use the keys, what operations they can perform, and under what conditions. This ensures that only authorized individuals have access to your data.
Audit and Monitoring
AWS KMS provides comprehensive audit and monitoring capabilities, allowing you to track and analyze the usage of your encryption keys. You can monitor key activity, detect potential security issues, and generate detailed audit reports for compliance purposes.
In summary, AWS KMS offers a range of features and benefits that make it an indispensable tool for data security. It provides secure key management, seamless integration with other AWS services, scalability and performance, granular access control, and audit and monitoring capabilities.
How AWS KMS Works
AWS KMS uses a combination of industry-leading techniques and advanced encryption algorithms to protect your data. Let’s take a closer look at how KMS works:
Key Generation
AWS KMS allows you to generate encryption keys using either AWS-managed keys or customer-managed keys. AWS-managed keys are created and managed by AWS on your behalf, while customer-managed keys are generated and managed by you. Both types of keys are protected using hardware security modules (HSMs) to ensure their integrity and confidentiality.
Key Storage
AWS KMS stores your encryption keys in a secure, centralized key management system. The keys are encrypted at rest and protected using strong encryption algorithms. KMS uses industry-standard key management practices to ensure the security and confidentiality of your keys.
Key Rotation
AWS KMS supports key rotation, allowing you to replace your encryption keys with new ones periodically. This helps to mitigate the risk of key compromise and ensures that your data remains protected. KMS makes it easy to rotate your keys without any impact on your applications or data.
Encryption and Decryption
AWS KMS provides encryption and decryption APIs that allow you to encrypt your data before storing it and decrypt it when needed. You can use KMS to encrypt data at rest in Amazon S3 or Amazon RDS or data in transit using encryption protocols such as SSL/TLS.
Access Control
AWS KMS allows you to define access control policies for your encryption keys. You can specify who can use the keys, what operations they can perform, and under what conditions. This ensures that only authorized individuals have access to your data.
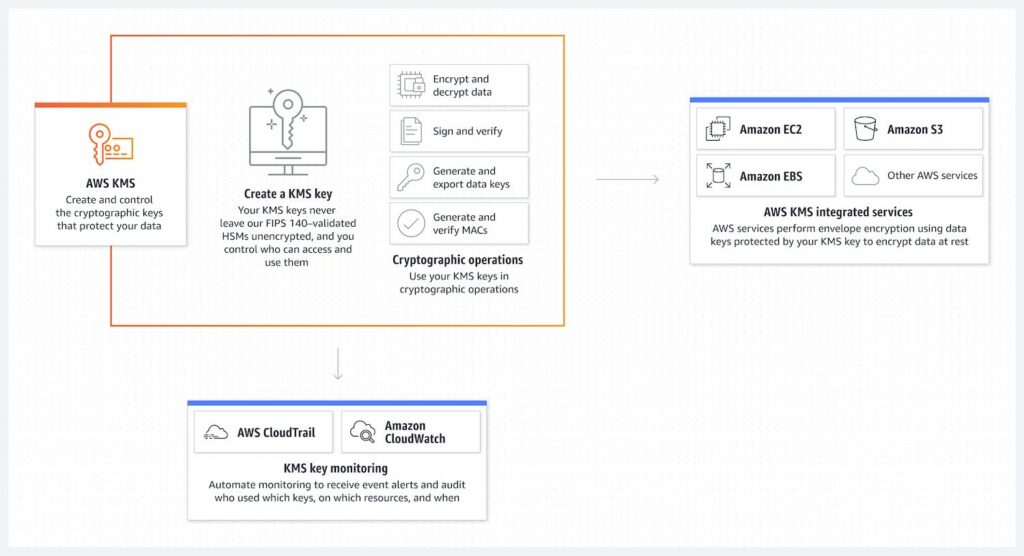
In summary, KMS uses a combination of key generation, key storage, key rotation, encryption and decryption, and access control to protect your data. By implementing KMS, you can ensure that your data remains secure and accessible only to authorized individuals.
Key Management Best Practices
To maximize the security and effectiveness of AWS KMS, it’s important to follow key management best practices. Here are some recommendations to consider:
Separation of Duties
Implement a separation of duties policy to ensure that no single individual has complete control over your encryption keys. This helps to mitigate the risk of key compromise and unauthorized access.
Key Rotation
Regularly rotate your encryption keys to mitigate the risk of key compromise. AWS KMS makes it easy to rotate your keys without any impact on your applications or data.
Key Storage
Store your encryption keys in a secure, centralized key management system like AWS KMS. Avoid storing keys in plaintext or in insecure locations.
Access Control
Define fine-grained access control policies for your encryption keys. Specify who can use the keys, what operations they can perform, and under what conditions. Regularly review and update these policies to ensure they align with your security requirements.
Monitoring and Auditing: Monitor the usage of your encryption keys and regularly audit their activity. This helps to detect potential security issues and ensure compliance with data privacy regulations.
By following these best practices, you can enhance your data’s security and maximize AWS KMS’s effectiveness.
Integrating AWS KMS into Your Existing Infrastructure
Integrating AWS KMS into your existing infrastructure is a straightforward process. Here are the steps to follow:
1. Evaluate Your Requirements
Determine your encryption needs and identify the data that needs to be protected. This will help you determine the type and number of encryption keys required.
2. Create Encryption Keys
Generate encryption keys using AWS KMS. Depending on your requirements, you can choose between AWS-managed keys or customer-managed keys.
3. Configure Integration
Configure your AWS services, such as Amazon S3 or Amazon RDS, to use AWS KMS for encryption. This can be done through the AWS Management Console, AWS Command Line Interface (CLI), or AWS SDKs.
4. Update Access Policies
Define access control policies for your encryption keys. Specify who can use the keys, what operations they can perform, and under what conditions.
5. Test and Monitor
Test the integration to ensure that your data is being encrypted and decrypted correctly. Monitor the usage of your encryption keys to detect any potential security issues.
By following these steps, you can seamlessly integrate KMS into your existing infrastructure and enhance the security of your data.
Using AWS KMS for Data Encryption and Decryption
AWS KMS provides a simple and secure way to encrypt and decrypt your data. Here’s how you can use AWS KMS for data encryption and decryption:
Encryption
To encrypt your data, you can use the AWS KMS encryption API. Simply provide the encryption key and the plaintext data, and KMS will return the encrypted data. You can then store the encrypted data in Amazon S3 or Amazon RDS, or transmit it securely over the network.
Decryption
To decrypt your data, you can use the AWS KMS decryption API. Provide the encryption key and the encrypted data, and KMS will return the decrypted plaintext. You can then access and use the decrypted data in your applications.
Envelope Encryption
AWS KMS supports envelope encryption, which allows you to encrypt large amounts of data efficiently. With envelope encryption, you generate a data encryption key (DEK) for each piece of data and encrypt the DEK with a master key. This allows you to encrypt and decrypt large amounts of data using a single master key.
Key Policies
AWS KMS allows you to define key policies to control access to your encryption keys. You can specify who can use the keys, what operations they can perform, and under what conditions. This ensures that only authorized individuals have access to your data.
By leveraging the encryption and decryption capabilities of KMS, you can protect your data at rest and in transit, ensuring that it remains secure and accessible only to authorized individuals.
Managing Access Permissions and Policies in AWS KMS
AWS KMS offers granular access control capabilities, allowing you to define fine-grained access permissions and policies for your encryption keys. Here’s how you can manage access permissions and policies in KMS:
Identity-Based Policies
AWS KMS supports identity-based policies, which allow you to control access to your encryption keys based on AWS Identity and Access Management (IAM) users and roles. You can specify who can use the keys, what operations they can perform, and under what conditions.
Key Policies
AWS KMS also supports key policies, which allow you to control access to your encryption keys at a more granular level. Key policies are similar to IAM policies but are specific to individual encryption keys. You can define key policies to specify who can use the keys, what operations they can perform, and under what conditions.
Permission Hierarchy
AWS KMS follows a permission hierarchy when evaluating access permissions. The hierarchy consists of key policies, IAM policies, and resource-based policies. By understanding the permission hierarchy, you can ensure that your access permissions are applied correctly.
Audit and Monitoring
AWS KMS provides comprehensive audit and monitoring capabilities, allowing you to track and analyze the usage of your encryption keys. You can monitor key activity, detect potential security issues, and generate detailed audit reports for compliance purposes.
By managing access permissions and policies in KMS, you can ensure that only authorized individuals have access to your encryption keys and data, enhancing the security of your confidential information.
Monitoring and Auditing Data Security with AWS KMS
Monitoring and auditing are essential components of a comprehensive data security strategy. AWS KMS provides robust monitoring and auditing capabilities, allowing you to track and analyze the usage of your encryption keys. Here’s how you can monitor and audit data security with KMS:
Key Activity
AWS KMS logs key activity, including key creation, rotation, and usage. You can access these logs through the AWS Management Console, AWS CLI, or AWS SDKs. By monitoring key activity, you can detect any unusual or suspicious behavior and take appropriate action.
CloudTrail Integration
AWS KMS integrates with AWS CloudTrail, a service that logs API calls made to AWS services. By enabling CloudTrail, you can capture detailed information about API calls made to KMS, including the identity of the caller, the time of the call, and the parameters used. This helps to ensure accountability and provides an audit trail for compliance purposes.
Alerts and Notifications
AWS KMS allows you to set up alerts and notifications for key events. You can configure alerts for specific key activities, such as key rotation or unauthorized key usage. By setting up alerts, you can proactively monitor the security of your encryption keys and respond quickly to any potential security issues.
Compliance Reporting
AWS KMS provides detailed audit reports that can be used for compliance purposes. These reports include information about key activity, access permissions, and key usage. By regularly generating and reviewing these reports, you can ensure that your data security practices align with regulatory requirements.
By leveraging the monitoring and auditing capabilities of KMS, you can proactively detect and respond to potential security issues, ensure compliance with data privacy regulations, and enhance the overall security of your data.
Conclusion: Why AWS KMS is Essential for Protecting Confidential Data
Protecting confidential data is a top business priority in today’s digital landscape. Implementing a robust encryption solution is essential, with cyber threats becoming increasingly sophisticated and data privacy regulations becoming stricter.
AWS Key Management Service (KMS) offers a comprehensive platform for managing encryption keys and protecting sensitive information. With features such as secure key management, seamless integration with other AWS services, scalability and performance, granular access control, and audit and monitoring capabilities, KMS provides the necessary tools to safeguard your data.






