Demystifying AWS CloudTrail: A Comprehensive Guide to Monitoring Your Cloud Environment
Are you looking for an in-depth guide on monitoring your cloud environment with AWS CloudTrail? Look no further! In this comprehensive guide, we will demystify AWS CloudTrail and provide you with all the information you need to effectively monitor and secure your cloud infrastructure.
AWS CloudTrail is a powerful tool that allows you to gain insights into the activities taking place within your AWS account. From tracking changes in your resources to monitoring user activity and detecting security issues, CloudTrail provides a wealth of information that can help you enhance the security and governance of your cloud environment.
Table of Contents
In this guide, we will cover everything you need to know about AWS CloudTrail, including its key features, benefits, and how to set it up. We will walk you through the process of enabling CloudTrail, configuring it to capture the desired events, and integrating it with other AWS services for enhanced visibility and control. We will also share best practices and tips for optimizing your CloudTrail setup.
Don’t let the complexities of monitoring and securing your cloud environment overwhelm you. With this comprehensive guide, you’ll be able to harness the full potential of AWS CloudTrail and ensure the safety and integrity of your cloud infrastructure. So let’s get started!
What is AWS CloudTrail?
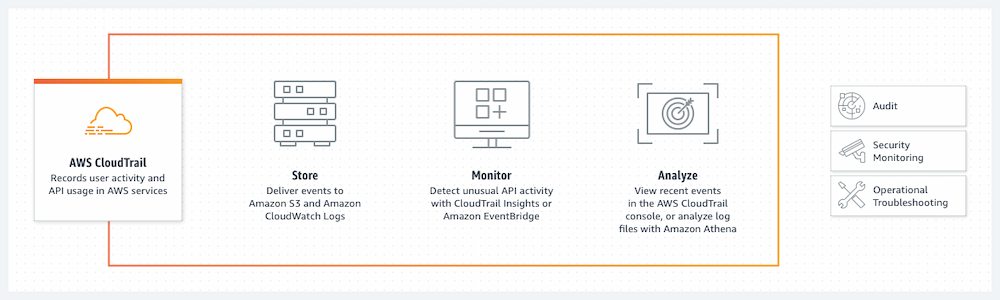
AWS CloudTrail is a service provided by Amazon Web Services (AWS) that enables you to track and record user activity and resource changes in your AWS account. It captures detailed information about API calls made by users, as well as events that occur within your AWS infrastructure. These events are stored in log files, which can be analyzed and used for various purposes, such as security analysis, compliance auditing, and troubleshooting.
CloudTrail provides a comprehensive view of activity within your AWS account, allowing you to identify who did what, when, and from where. It records important information, such as the identity of the caller, the source IP address, the action performed, and the response received. This level of visibility can be invaluable for monitoring, understanding, and managing your AWS environment.
Why is monitoring your cloud environment important?
Monitoring your cloud environment is crucial for several reasons. Firstly, it helps you ensure the security and compliance of your infrastructure. By tracking user activity and resource changes, you can detect and respond to any unauthorized or suspicious actions promptly. This can help prevent security breaches and protect your sensitive data.
Secondly, monitoring allows you to optimize the performance and efficiency of your cloud environment. By analyzing the usage patterns and resource utilization, you can identify opportunities for cost optimization, capacity planning, and performance improvements. This can help you make informed decisions and maximize the value of your cloud investment.
Lastly, monitoring your cloud environment is essential for meeting regulatory and compliance requirements. Many industries have specific data protection and privacy regulations that must be adhered to. By monitoring and auditing your cloud infrastructure, you can demonstrate compliance and provide evidence of the controls and safeguards in place.
Key features and benefits of AWS CloudTrail
AWS CloudTrail offers a range of features and benefits that make it an indispensable tool for monitoring your cloud environment.
Detailed Event Logging
CloudTrail captures detailed information about API calls and events within your AWS account. This includes the identity of the caller, the source IP address, the action performed, and the response received. This level of granularity allows you to gain insights into the activities taking place within your infrastructure.
Real-time Monitoring
CloudTrail provides real-time monitoring of your AWS account, allowing you to receive immediate alerts and notifications when specific events occur. This enables you to take prompt action in response to security incidents or policy violations.
Centralized Log Management
CloudTrail logs are stored in Amazon S3, providing a centralized and durable repository for your event data. This makes it easy to search, analyze, and retain logs for compliance and auditing purposes.
Integration with AWS Services
CloudTrail integrates seamlessly with other AWS services, such as AWS CloudWatch and AWS Config. This allows you to leverage the power of these services for enhanced visibility, automation, and control over your cloud environment.
Multi-region Support
CloudTrail supports multi-region logging, allowing you to capture events from different AWS regions in a single trail. This is particularly useful for organizations with a global presence or those looking to consolidate their logs for analysis and reporting.
Setting up AWS CloudTrail
Setting up AWS CloudTrail is a straightforward process that involves a few simple steps.
- Create a trail: To get started, you need to create a trail, which is a configuration that specifies the settings for capturing and storing your CloudTrail logs. You can create a trail using the AWS Management Console, AWS CLI, or AWS CloudFormation templates.
- Configure trail settings: Once you have created a trail, you can configure the settings according to your requirements. This includes specifying the S3 bucket where your logs will be stored, enabling log file encryption, and defining the events that you want to capture.
- Enable the trail: After configuring the trail settings, you need to enable the trail to start capturing events. Once enabled, CloudTrail will begin logging events and storing them in the specified S3 bucket.
- Verify the trail status: Finally, you should verify the status of your trail to ensure that it is active and functioning correctly. You can do this by checking the trail status in the CloudTrail console or using the AWS CLI.
By following these steps, you can quickly set up AWS CloudTrail and start capturing events within your AWS account.
Configuring AWS CloudTrail for Monitoring
Once you have set up AWS CloudTrail, you can configure it to capture the desired events and customize its behaviour according to your requirements.
Event Selection
AWS CloudTrail allows you to specify the events that you want to capture in your logs. By default, CloudTrail captures all management events, such as API calls made to create, modify, or delete AWS resources. However, you can also choose to capture data events, which include read and write operations on specific resources, such as S3 buckets or DynamoDB tables.
To configure event selection, you can use the AWS Management Console, AWS CLI, or CloudTrail API. You can specify the events using a combination of service, resource type, and specific operations. This level of granularity allows you to focus on the events that are most relevant to your monitoring and auditing needs.
Log File Encryption
To enhance the security of your CloudTrail logs, you can enable log file encryption. When enabled, CloudTrail will encrypt your log files using AWS Key Management Service (KMS) before storing them in the S3 bucket. This ensures that your logs are protected from unauthorized access and tampering.
You can choose to use the default encryption key provided by AWS KMS or specify a custom KMS key for enhanced control over the encryption process. Additionally, you can enable log file integrity validation to verify the integrity of your log files and detect any unauthorized modifications.
CloudTrail Insights
CloudTrail Insights is a feature that helps you identify and respond to unusual activity within your AWS account. It uses machine learning algorithms to analyze your CloudTrail logs and detect patterns that may indicate potential security issues or operational anomalies.
By enabling CloudTrail Insights, you can receive actionable insights and recommendations based on the analysis of your log data. This can help you proactively detect and mitigate security threats, such as unauthorized access attempts or unusual resource modifications.
CloudTrail Insights Event Insights
In addition to CloudTrail Insights, AWS offers a feature called CloudTrail Insights Event Insights. This feature provides additional context and analysis for specific events captured in your CloudTrail logs. It automatically identifies related events and presents them in a timeline view, allowing you to understand the full context and impact of an event.
CloudTrail Insights Event Insights can help you investigate security incidents, troubleshoot operational issues, and gain a deeper understanding of the activities within your AWS account.
Understanding and Analyzing CloudTrail Logs
Once you have configured AWS CloudTrail and captured events within your AWS account, you can start analyzing the log data to gain insights and identify potential security issues.
CloudTrail logs are stored in JSON format and can be accessed from the S3 bucket specified during the trail setup. Each log file contains multiple log entries, each representing an event that occurred within your AWS account.
To analyze CloudTrail logs, you can use various tools and techniques, such as:
AWS CloudTrail Console
The CloudTrail console provides a user-friendly interface for searching, filtering, and analyzing your log data. You can use the console to search for specific events, view event details, and export log data for further analysis.
AWS CLI
The AWS CLI allows you to interact with CloudTrail and perform various operations, such as searching for events, filtering logs, and exporting log files. It provides a command-line interface that can be integrated into your scripts or used for ad-hoc analysis.
Third-party Tools
There are several third-party tools available that can help you analyze and visualize your CloudTrail logs. These tools provide advanced features, such as log aggregation, anomaly detection, and real-time monitoring, to enhance your log analysis capabilities.
When analyzing CloudTrail logs, it is essential to look for patterns, anomalies, and suspicious activities. You should pay attention to events related to resource modifications, privilege escalations, access attempts, and changes in security group configurations. By analyzing the logs regularly, you can identify potential security issues and take appropriate actions to mitigate them.
Integrating AWS CloudTrail with Other AWS Services
AWS CloudTrail can be integrated with other AWS services to enhance the visibility, automation, and control over your cloud environment. Here are some of the key integrations:
AWS CloudWatch
CloudTrail can be integrated with AWS CloudWatch to provide real-time monitoring and alerting capabilities. By configuring CloudWatch alarms, you can receive notifications when specific events occur, such as unauthorized API calls or changes in resource configurations.
AWS Config
CloudTrail can be used as a data source for AWS Config, which is a service that provides detailed inventory, configuration history, and change notifications for your AWS resources. By integrating CloudTrail with AWS Config, you can gain a comprehensive view of your resource configurations and track changes over time.
AWS Lambda
CloudTrail can trigger AWS Lambda functions in response to specific events captured in your logs. This allows you to automate actions and workflows based on the events occurring within your AWS account. For example, you can configure a Lambda function to send notifications or perform remediation actions when a security event is detected.
AWS SNS
CloudTrail can publish events to Amazon SNS (Simple Notification Service), which is a fully managed messaging service. By subscribing to the CloudTrail SNS topic, you can receive notifications in real-time when specific events occur. This can help you stay informed about critical events and take immediate action.
By integrating CloudTrail with these services, you can enhance your monitoring and response capabilities, automate routine tasks, and improve the overall security and compliance of your cloud environment.
Best Practices for AWS CloudTrail Monitoring
To get the most out of AWS CloudTrail and ensure effective monitoring of your cloud environment, it is essential to follow best practices. Here are some recommendations:
Enable multi-region logging
If your AWS account operates in multiple regions, consider enabling multi-region logging for CloudTrail. This allows you to capture events from all regions in a single trail, providing centralized visibility and simplifying log analysis.
Regularly review and analyze logs
Make it a practice to regularly review and analyze your CloudTrail logs. Look for patterns, anomalies, and suspicious activities that may indicate security issues. Consider setting up automated log analysis and alerting to streamline this process.
Monitor critical events
Focus on monitoring critical events that have the potential to impact the security and compliance of your environment. These may include changes to IAM roles and policies, modifications to security groups, or access attempts by unauthorized users.
Enable CloudTrail Insights
Take advantage of the CloudTrail Insights feature to proactively detect security threats and operational anomalies. Enable event notifications and recommendations to receive actionable insights based on the analysis of your log data.
Regularly update and review IAM police
Keep your IAM (Identity and Access Management) policies up to date and review them regularly. Ensure that least privilege principles are followed and that access permissions are regularly reviewed and revoked when no longer needed.
Implement log file encryption
Enable log file encryption to protect your CloudTrail logs from unauthorized access and tampering. Consider using a custom KMS key for enhanced control over the encryption process.
Backup and retain logs
Implement a backup and retention strategy for your CloudTrail logs. Consider storing backups in a separate AWS account or region for added resilience. Retain logs for the required period to meet compliance and auditing requirements.
By following these best practices, you can ensure that AWS CloudTrail is effectively monitoring your cloud environment and providing the necessary insights to enhance security and compliance.
AWS CloudTrail vs. Other Cloud Monitoring Tools
While AWS CloudTrail is a powerful tool for monitoring your AWS environment, it is essential to understand how it compares to other cloud monitoring tools. Here are some key differences:
AWS CloudWatch
AWS CloudWatch is a monitoring and observability service that provides real-time insights into the performance and health of your AWS resources. While CloudTrail focuses on capturing API calls and events, CloudWatch provides more comprehensive monitoring capabilities, such as metrics, logs, and alarms.
AWS Config
AWS Config is a service that provides detailed inventory, configuration history, and change notifications for your AWS resources. While CloudTrail captures events, AWS Config focuses on recording and tracking resource configurations over time. Both services can be used together to gain a comprehensive view of your environment.
Third-party Monitoring Tools
There are several third-party monitoring tools available that offer more advanced features and capabilities compared to AWS CloudTrail. These tools provide features such as log aggregation, anomaly detection, and real-time monitoring across multiple cloud providers. However, they may come at an additional cost and require additional setup and configuration.
When choosing a monitoring solution for your cloud environment, consider your specific requirements, budget, and the level of visibility and control you need. AWS CloudTrail is an excellent choice for monitoring AWS-specific events and activity, but you may need to complement it with other tools for a more comprehensive monitoring strategy.
Conclusion: Enhancing Security and Compliance with AWS CloudTrail
Monitoring your cloud environment is crucial for ensuring the security, compliance, and performance of your AWS infrastructure. AWS CloudTrail provides a powerful and comprehensive solution for capturing and analyzing events within your AWS account.
In this comprehensive guide, we have covered AWS CloudTrail and provided you with all the information you need to effectively monitor and secure your cloud environment. We have covered the key features and benefits of CloudTrail, outlined the setup and configuration process, and discussed best practices for monitoring and analyzing your CloudTrail logs.
By following the recommendations and best practices outlined in this guide, you can harness the full potential of AWS CloudTrail and ensure the safety and integrity of your cloud infrastructure. Don’t let the complexities of monitoring and securing your cloud environment overwhelm you. With AWS CloudTrail, you have a powerful tool at your disposal to gain visibility, detect security issues,



