In today’s digital landscape, cybersecurity has become a critical concern for organizations of all sizes. The rise of cloud computing has brought about new types of threats that traditional security measures struggle to address. This is where AWS GuardDuty enters the picture as your ultimate guardian angel for cloud threat detection.
Safeguarding your cloud infrastructure is no longer a daunting task with GuardDuty’s advanced machine-learning algorithms and comprehensive threat intelligence. It constantly monitors your AWS environment, detecting unauthorized access, malicious activity, and potential data breaches. With real-time alerts, you can stay one step ahead and respond swiftly to any security incident.
Table of Contents
What sets GuardDuty apart from other security solutions? Its seamless integration with other AWS services and ability to automatically scale with your cloud infrastructure make it a game-changer. Its straightforward setup and user-friendly interface ensure you can start protecting your cloud assets without any hassle.
Join us as we delve deeper into the powerful features and benefits of AWS GuardDuty. Don’t let cloud security keep you up at night – let GuardDuty be your trusted ally in the ever-evolving cybersecurity battleground.
Understanding Cloud Threats and the Need for Threat Detection
The shift to cloud computing has revolutionized how organizations operate, providing numerous benefits such as scalability, flexibility, and cost efficiency. However, this transformation also introduces new challenges, particularly in cybersecurity. As more businesses migrate their operations to the cloud, cybercriminals quickly exploit any vulnerabilities they can find. From unauthorized access to data breaches, the consequences of a cloud security incident can be devastating.
Traditional security measures, such as firewalls and intrusion detection systems, are not enough to protect your cloud infrastructure from these evolving threats. That’s where AWS GuardDuty comes in. By leveraging advanced machine learning algorithms and comprehensive threat intelligence, GuardDuty provides an extra layer of defense to your AWS environment. It analyzes vast amounts of data in real-time, enabling it to detect and respond to threats more effectively than ever before.
How AWS GuardDuty Works
Amazon GuardDuty is a sophisticated threat detection service that provides continuous monitoring of your AWS accounts and workloads to identify malicious activity and deliver detailed security findings for effective visibility and remediation. This service operates by continuously analyzing various data sources within your AWS environment, such as VPC flow logs, CloudTrail event logs, and DNS logs. It utilizes advanced techniques including anomaly detection, machine learning, and behavioral modeling, and integrates threat intelligence feeds from AWS and leading third-party sources.
GuardDuty is adept at exposing a wide array of threats quickly and efficiently. It can detect issues such as unauthorized or unusual activities, compromised instances, and data exfiltration attempts. The service is designed to seamlessly scale threat detection capabilities across your AWS environment, ensuring that your security measures scale accordingly as your cloud infrastructure grows. This scalability is crucial for maintaining consistent security monitoring and threat detection as your AWS usage evolves.
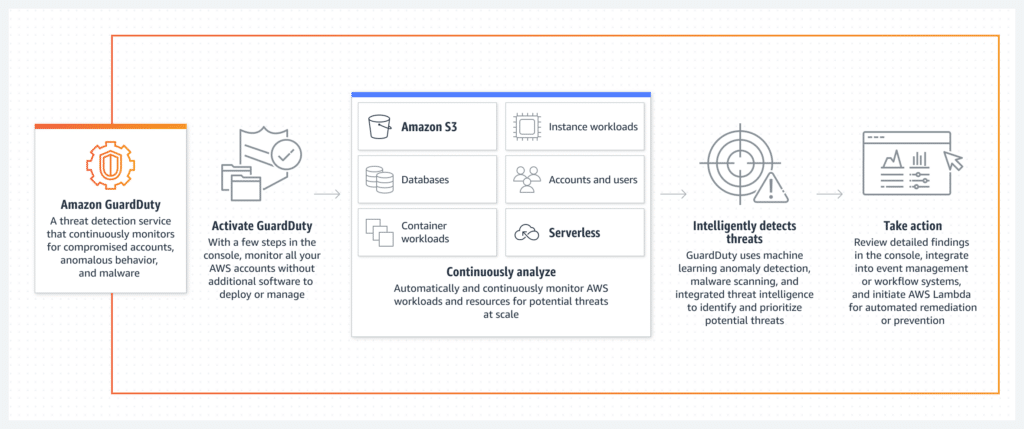
Features and Capabilities of AWS GuardDuty
AWS GuardDuty offers a wide range of features and capabilities that make it an indispensable tool for cloud security. Let’s explore some of its key functionalities:
Continuous Monitoring
GuardDuty constantly analyzes data from various AWS sources, including VPC flow logs, CloudTrail logs, and DNS logs. This comprehensive monitoring ensures that any suspicious activity or potential threats are promptly identified.
Threat Detection
Leveraging machine learning algorithms and threat intelligence feeds, GuardDuty can detect a wide range of threats, including unauthorized access attempts, compromised instances, and data exfiltration attempts.
Real-time Alerts
When GuardDuty detects a potential threat, it generates real-time alerts that are sent to the AWS Management Console, Amazon CloudWatch, or an email notification. These alerts provide detailed information about the nature of the threat, enabling you to respond swiftly and effectively.
Scalability
GuardDuty automatically scales with your cloud infrastructure, ensuring that it can handle the growing volume of data generated by your AWS environment. This scalability ensures that GuardDuty’s performance remains consistent, regardless of the size of your infrastructure.
Easy Integration
GuardDuty seamlessly integrates with other AWS services, such as AWS CloudTrail and AWS Security Hub. This integration allows you to consolidate security alerts and streamline incident response processes.
Setting up AWS GuardDuty in Your Cloud Environment
Getting started with AWS GuardDuty is a straightforward process. Here’s a step-by-step guide to help you set up GuardDuty in your AWS environment:
Enable GuardDuty
To get started, navigate to the AWS Management Console and search for GuardDuty. Click on “Enable GuardDuty” to activate the service in your AWS account.
Choose the AWS Regions
GuardDuty is available in multiple AWS regions. Select the regions where you want GuardDuty to monitor your AWS environment.
Configure Data Sources
GuardDuty relies on various data sources to analyze and detect threats. Enable the necessary data sources, such as VPC flow logs and CloudTrail logs, to ensure comprehensive coverage.
Set Up Monitoring Frequency
GuardDuty allows you to choose the frequency at which it analyzes your data. You can select either a continuous monitoring option or a schedule that best suits your needs.
Configure Alert Notifications
Customize the alert notifications to ensure they reach the right stakeholders on time. You can choose to receive alerts via email or Amazon CloudWatch or integrate GuardDuty with other AWS security services.
Review and Confirm
Before finalizing the setup, review the configuration settings to ensure everything is in order. Once satisfied, click “Confirm” to activate GuardDuty in your AWS environment.
By following these simple steps, you can quickly start leveraging the power of AWS GuardDuty to enhance the security of your cloud infrastructure.
Configuring and Customizing GuardDuty Alerts and Notifications
AWS GuardDuty provides a range of options for configuring and customizing alerts and notifications. This flexibility allows you to tailor the alerting system to meet your specific requirements. Here are some key aspects to consider when configuring GuardDuty alerts:
Severity Levels
GuardDuty assigns a severity level to each detected threat, ranging from low to high. You can customize the threshold for each severity level to ensure that you receive alerts only for the most significant threats.
Whitelisting Trusted IP Addresses
If trusted IP addresses are regularly accessing your AWS environment, you can whitelist them to avoid receiving unnecessary alerts. This helps reduce alert fatigue and ensures that you focus on the most critical threats.
Suppressing False Positives
GuardDuty’s machine-learning algorithms are designed to minimize false positives. However, in some cases, certain activities may trigger false alarms. GuardDuty allows you to suppress specific types of alerts to avoid unnecessary noise.
Integrating with Incident Response Processes
To streamline your incident response processes, you can integrate GuardDuty with other AWS services, such as AWS Security Hub or AWS Lambda. This integration ensures that alerts are automatically forwarded to your incident response team, enabling them to take immediate action.
By fine-tuning GuardDuty’s alerting and notification settings, you can ensure that you receive timely and relevant alerts, allowing you to respond swiftly to potential threats.
Analyzing and Responding to Detected Threats
When GuardDuty detects a potential threat in your AWS environment, it’s crucial to analyze the situation and respond accordingly. Here’s a recommended approach for analyzing and responding to detected threats:
Investigate the Alert
When you receive an alert from GuardDuty, carefully review the details provided. Pay attention to the severity level, affected resources, and any additional context that can help you understand the nature of the threat.
Gather Additional Information
To gain a deeper understanding of the threat, gather additional information from various sources. This may include reviewing logs, analyzing network traffic, or examining relevant security events.
Assess the Impact
Evaluate the potential impact of the threat on your AWS environment and business operations. Consider the affected data’s sensitivity, the affected resources’ criticality, and the potential consequences of a successful attack.
Contain the Threat
Once you have assessed the impact, take immediate steps to contain the threat. This may involve isolating affected resources, revoking privileges, or shutting down compromised instances.
Remediate and Recover
After containing the threat, focus on remediating the vulnerabilities that allowed the attack to occur. This may involve patching software, updating configurations, or enhancing access controls. Additionally, consider implementing measures to prevent similar incidents in the future.
Learn and Improve
Every security incident provides an opportunity to learn and improve your security posture. Conduct a post-incident analysis to identify lessons learned, update security policies and procedures, and enhance your overall security infrastructure.
By following this approach, you can effectively respond to detected threats and minimize the potential impact on your AWS environment.
Best Practices for Maximizing the Effectiveness of AWS GuardDuty
To fully leverage the power of AWS GuardDuty, it’s essential to follow best practices that maximize its effectiveness. Here are some key recommendations to consider:
Enable GuardDuty in All Relevant AWS Regions
If your organization operates in multiple AWS regions, ensure that GuardDuty is enabled in all of them. This ensures comprehensive coverage and visibility across your cloud infrastructure.
Regularly Review and Fine-tune Alerting Settings
GuardDuty’s alerting system should be regularly reviewed and adjusted based on your organization’s evolving needs. Fine-tune the severity thresholds, whitelist trusted IP addresses, and suppress false positives to optimize the alerting process.
Integrate GuardDuty with Other AWS Security Services
GuardDuty works seamlessly with other AWS security services, such as AWS Security Hub and Amazon Detective. By integrating these services, you can consolidate your security alerts, streamline incident response, and gain a holistic view of your security posture.
Continuously Monitor and Analyze GuardDuty Findings
GuardDuty generates valuable findings that can provide insights into potential vulnerabilities and security risks. Regularly monitor and analyze these findings to identify areas for improvement and proactively address emerging threats.
Stay up-to-date with GuardDuty Enhancements and New Features
AWS regularly updates and enhances GuardDuty with new features and capabilities. Stay informed about these updates and leverage the latest functionalities to improve your cloud security.
By following these best practices, you can ensure that AWS GuardDuty remains a powerful ally in your cloud security arsenal.
Integrating GuardDuty with Other AWS Security Services
AWS GuardDuty is designed to work seamlessly with other AWS security services, creating a comprehensive security ecosystem for your cloud infrastructure. Here are some key AWS security services that can be integrated with GuardDuty:
AWS Security Hub
By integrating GuardDuty with AWS Security Hub, you can centralize and prioritize security findings from multiple AWS services. This integration provides a consolidated view of your security alerts, simplifying incident response and enhancing your overall security posture.
Amazon CloudWatch
GuardDuty can send real-time alerts to Amazon CloudWatch, allowing you to create custom dashboards, set up automated actions, and trigger additional security measures. This integration enhances your ability to respond swiftly to potential threats.
AWS Lambda
With AWS Lambda, you can automate response actions based on GuardDuty alerts. For example, you can configure Lambda functions to automatically isolate compromised instances, revoke privileges, or perform forensic analysis on affected resources.
Amazon Detective
Amazon Detective leverages GuardDuty findings to provide detailed visualizations and actionable insights into potential security threats. By integrating GuardDuty with Amazon Detective, you can gain a deeper understanding of security incidents, identify trends, and improve your incident response processes.
By integrating GuardDuty with these AWS security services, you can create a robust security ecosystem that enhances your ability to detect, respond to, and mitigate potential threats in your cloud environment.
Conclusion – Leveraging AWS GuardDuty for Proactive Cloud Security
In today’s rapidly evolving threat landscape, cloud security is of paramount importance. With the rise of cloud computing, traditional security measures are no longer sufficient to protect your valuable assets. This is where AWS GuardDuty shines as your ultimate guardian angel for cloud threat detection.
By leveraging advanced machine learning algorithms, comprehensive threat intelligence, and seamless integration with other AWS services, GuardDuty provides unparalleled protection for your AWS environment. Its real-time alerts, scalability, and user-friendly interface make it a game-changer in the world of cloud security.
Don’t let cloud security keep you up at night. Embrace the power of AWS GuardDuty and let it be your trusted ally in the ever-evolving cybersecurity battleground. With GuardDuty by your side, you can proactively detect, respond to, and mitigate potential threats, ensuring the safety and integrity of your cloud infrastructure.




